Office 365 low hanging security fruits - Mail tagging
This part is focused once again on mail traffic and its attack vectors. Specifically, I wanted to tag all incoming mails in Office 365 Exchange, which are not coming from trusted domains. This is really easy to implement with Exchange Online rules and doesn’t even require any kind of powershell knowlegde, so every O365 should have implemented this policy in their environment.
This is a multi part security series for O365 with the following articles:
A lot of cyber-attacks on companies start of with a (spear) phishing mail to the employees, as I have mentioned before. A common technique for this approach is to register a domain which looks very similar to their target domain e.g. payment@amzaonwebservices.com instead of payment@amazonwebservices.com, as the difference might be hard to spot for the untrained employee. Another option for the attacker is to use a domain with non-Latin alphabets such es Ukrainian, Cyrillic etc. This kind of spoofing can abuse the Unicode system for IDNs to create very real looking domains just with a different meaning, as the Unicode system has more than 136k characters. A very detailed dive-in about this kind of technique can be found here. In summary there are many ways to spoof an email address to fool the phishing victim and I needed a way to flag these kinds of mails to the user, which look like they are from inside the company, but are actually from an external domain.
The way to accomplish this requirement is by automatically tagging mails, which don’t originate from trusted/known domains. Obviously, you don’t want to block them (could lead to an angry CIO storming your office), but rather make the user aware of it. It is actually rather easy to do this with the 0365 Exchange Control Panel (ECP).
You want to discuss this rule with your supervisor first and make sure everyone in the company is aware of it. Otherwise the whole point of raising awareness for these kinds of mails is not achieved plus you might get a lot of confused calls and mails from users.
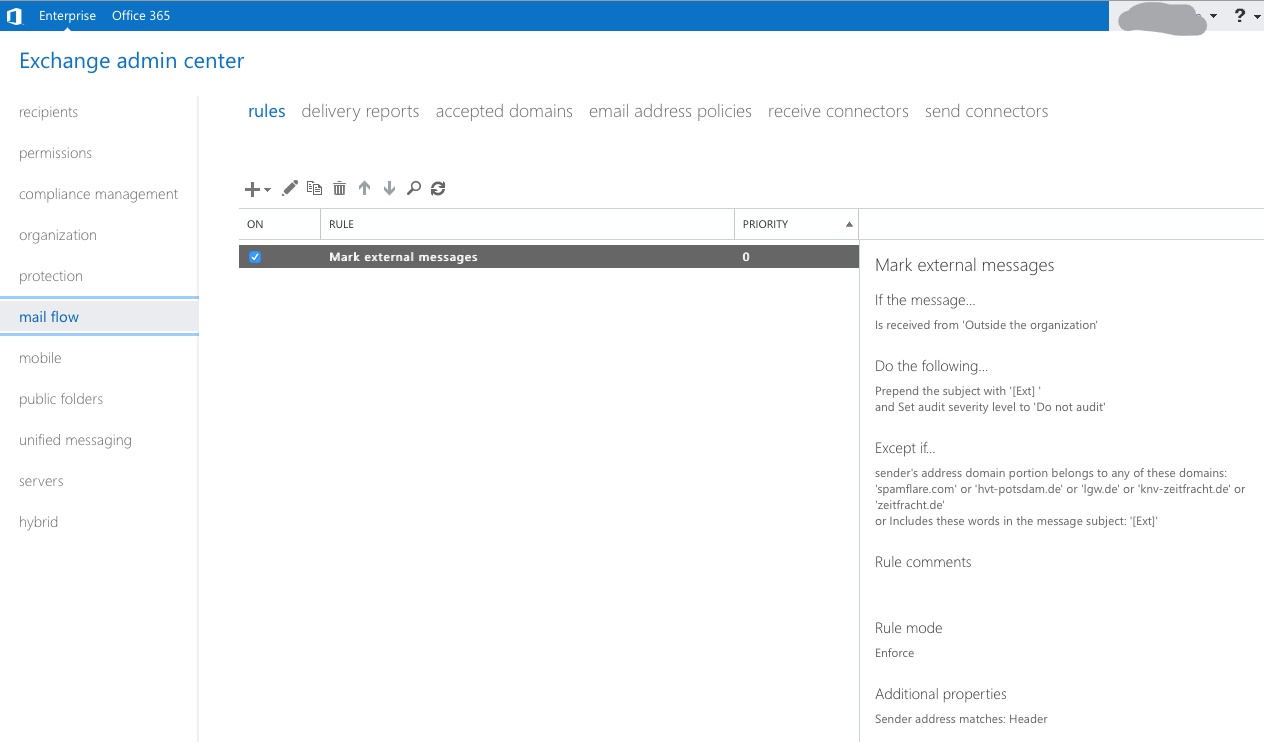
- Navigate to mail flow and add a new policy under the
ruletab - You want to select modify message
- Name the rule accordingly
- Set the rule to senders outside of organization
- Set the tagging rule accordingly.
I always use something short but eye-catching, so the recipient gets a short heads-up, in this case[Ext] - You want to add exception for the tag so you don’t end up with a recursive mail subject, such as (
[Ext]:[Ext]:[Ext]) - You also want to white-list all friendly domains to ease to process for users and create less false positives
- Finally, you want to test the rule and add then add it to your ruleset
That’s it, you are already done. As mentioned before, you want to spread the word about this measure first to prepare the users and train them to look out for these kind of tags.