

Copilot
Copilot Studio
Copilot Studio is a platform for quickly and efficiently creating solutions and applications based on AI models such as GPT-4 or other popular models. It offers the possibility to develop interactive and productivity-enhancing applications that can then be integrated into various Microsoft services (Teams, SharePoint, Office, etc.).

Copilot, AI
Microsoft Copilot & AI - AI - Copilot - Microsoft Graph
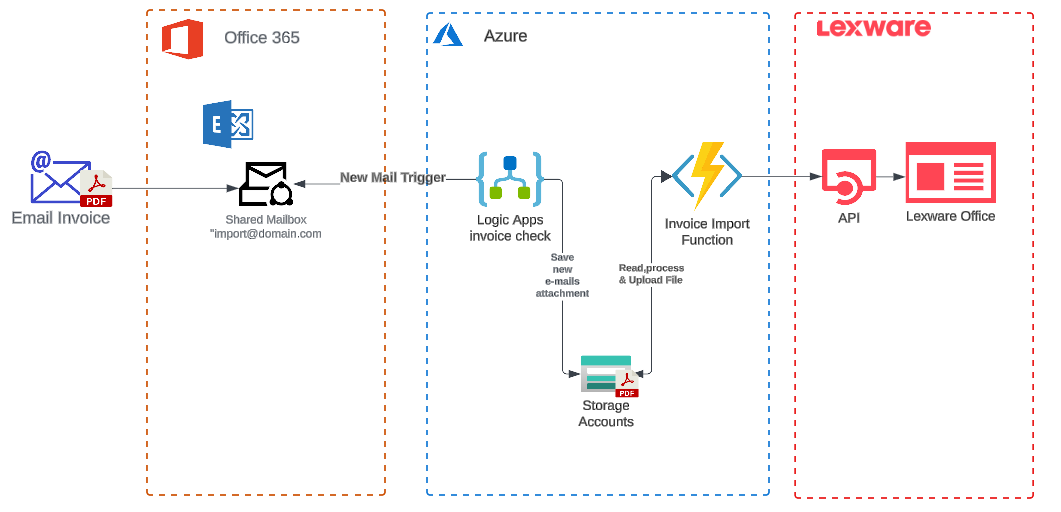
This post introduces the topic of Copilot and the basics, different deployment scenarios and possibilities that currently exist in the Microsoft cosmos. What everyday problems Copliot, Power Platform can help with and what possibilities Azure AI Services provide.
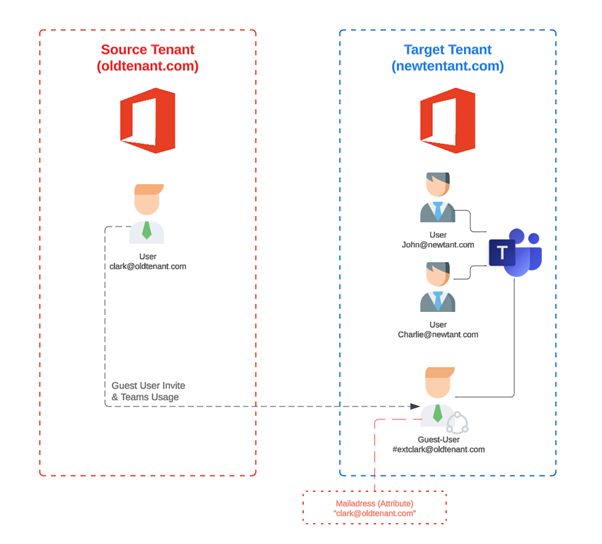
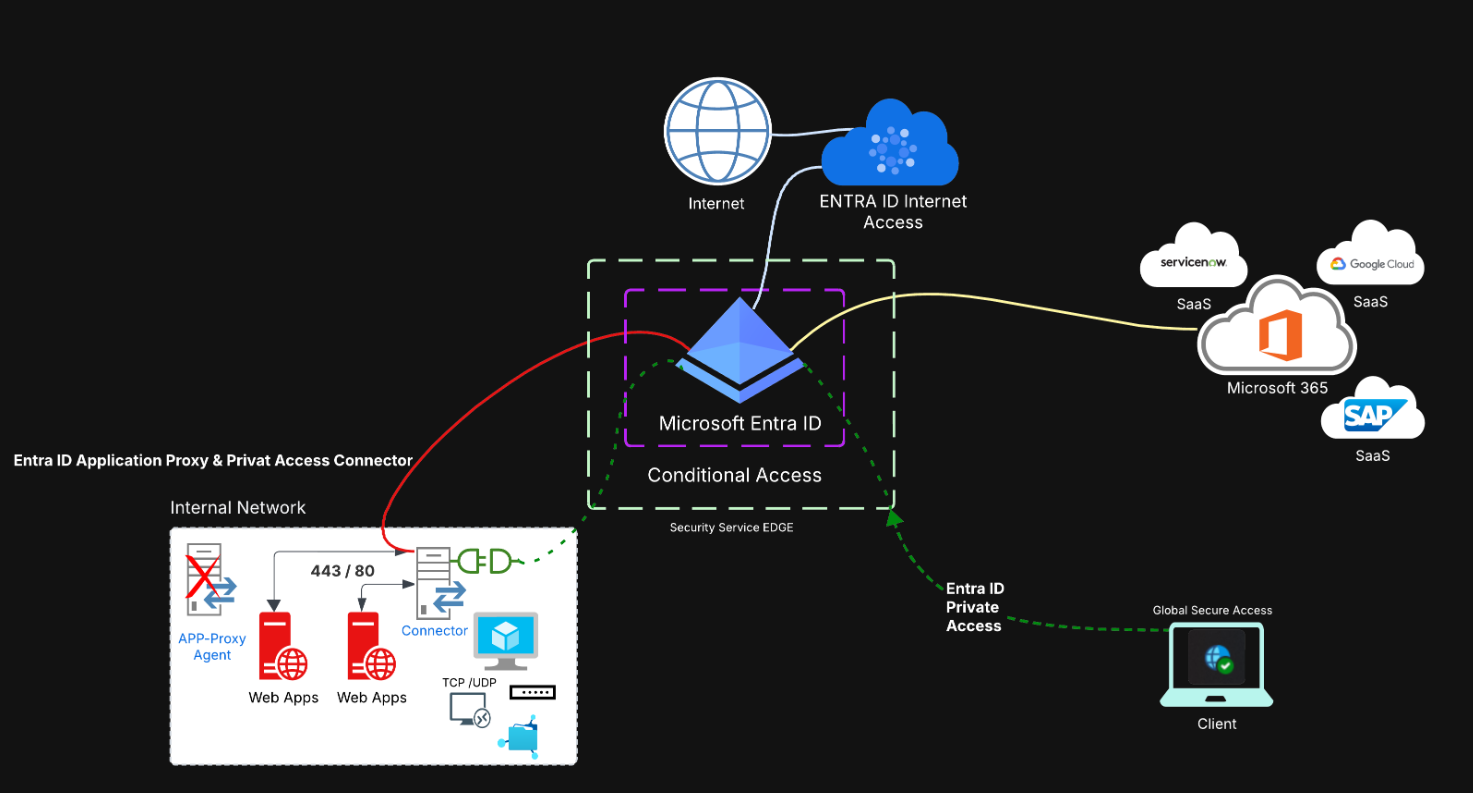
Entra ID
Office 365 Tenant to Tenant Migration Entra ID - Guest User Part 7
In the first part of the blog series, we took a look at the topic of planning and selecting the migration scenario and developed a long-term strategy based on the business and technical requirements and defined how the tenant migration should be implemented schematically.

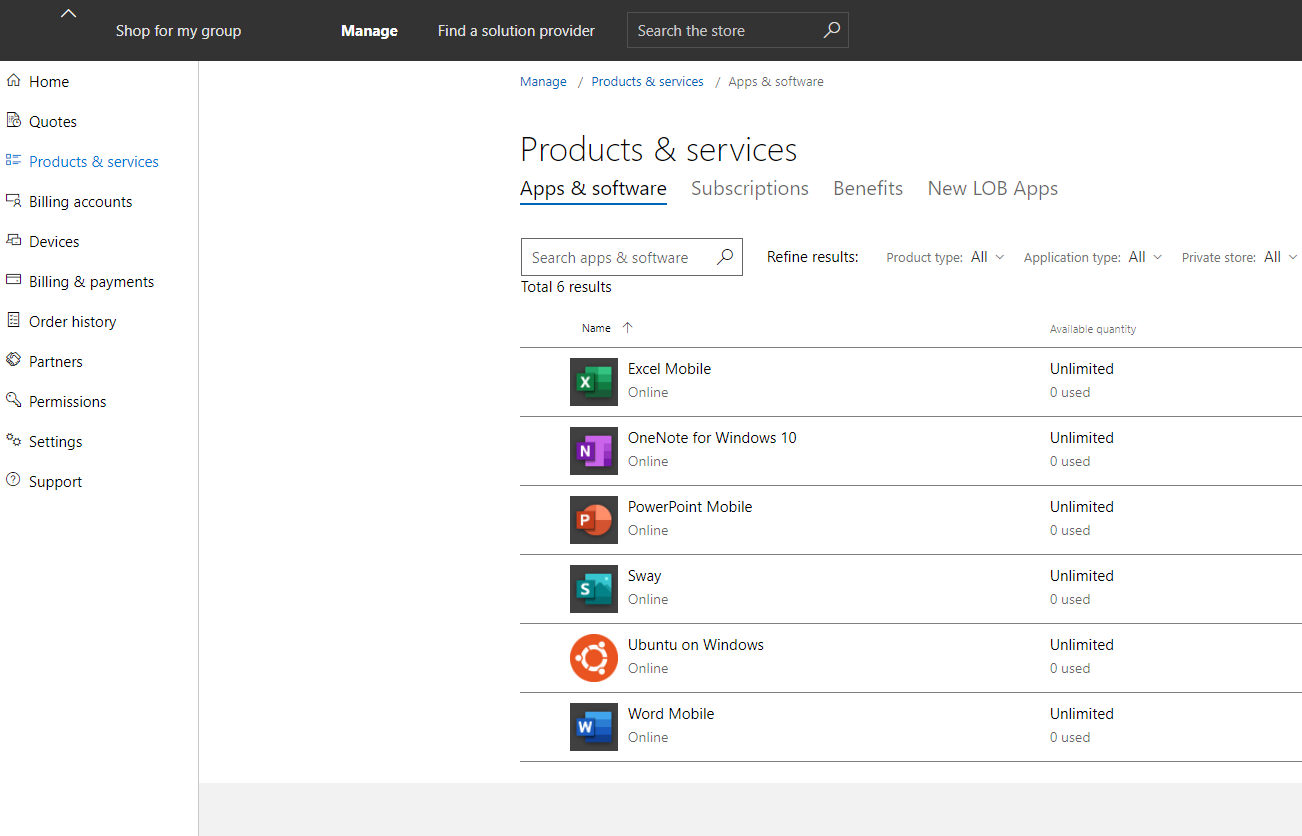
Office 365
Office 365 Tenant to Tenant Migration Stores Part 6
In the first part of the blog series, we took a look at the topic of planning and selecting the migration scenario and developed a long-term strategy based on the business and technical requirements and defined how the tenant migration should be implemented schematically.
